Symmetric-key cryptography
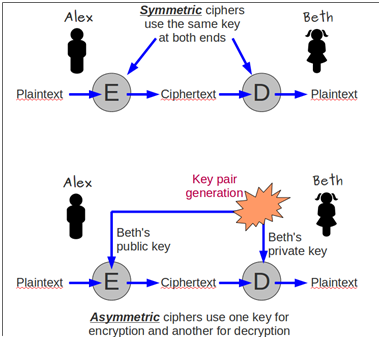
Symmetric-key cryptography is a cryptographic technique that uses a single secret key to both encrypt and decrypt data. This key is shared between the sender and receiver of the encrypted information, hence the name “symmetric” key cryptography.
In symmetric-key cryptography, the encryption process takes plaintext data and a secret key as inputs and produces ciphertext as output. The decryption process takes the ciphertext and the same secret key as inputs and produces the original plaintext.
The security of symmetric-key cryptography relies on keeping the secret key secret. If an attacker gains access to the secret key, they can easily decrypt the ciphertext and access the original plaintext.
Examples of symmetric-key cryptography include block ciphers like AES (Advanced Encryption Standard) and DES (Data Encryption Standard), and stream ciphers like RC4 (Rivest Cipher 4). These algorithms are widely used to provide confidentiality in various applications, such as secure communications over the internet, secure storage of data, and protection of sensitive information.
History of Symmetric-key Cryptography
The history of symmetric-key cryptography dates back to ancient times when secret codes were used to send messages. However, the modern era of symmetric-key cryptography began in the early 20th century with the invention of rotor machines, which were electro-mechanical devices that used rotors to encrypt and decrypt messages.
During World War II, symmetric-key cryptography became a critical tool for military communication. The Germans used the Enigma machine, which was a rotor machine, to encrypt their messages. The Allies eventually cracked the Enigma code, which was a major turning point in the war. This led to the development of more advanced rotor machines such as the British Typex and the American SIGABA.
After the war, the focus of symmetric-key cryptography shifted from rotor machines to electronic encryption devices. The Data Encryption Standard (DES) was developed in the 1970s by IBM and adopted by the US government as a standard for secure communications. DES used a 56-bit key and a block cipher structure to encrypt data. However, the growing processing power of computers eventually made DES vulnerable to brute force attacks.
To address this vulnerability, the Advanced Encryption Standard (AES) was developed in the 1990s as a replacement for DES. AES uses a block cipher structure like DES but has a variable key length of 128, 192, or 256 bits. AES is widely used today in various applications that require strong encryption, such as secure communications over the internet and secure storage of data.
In addition to AES, other symmetric-key encryption algorithms have been developed over the years, such as Blowfish, RC4, and Twofish. These algorithms have different strengths and weaknesses, and they are used in various applications depending on the specific requirements for encryption.
Overall, the history of symmetric-key cryptography has been driven by the need for secure communication and the advancements in technology. As technology continues to evolve, symmetric-key cryptography will continue to play an important role in ensuring the security of information in various applications.
Applications of Symmetric-key Cryptography
Symmetric-key cryptography has a wide range of applications in various fields, where confidentiality and privacy are critical. Some of the most common applications of symmetric-key cryptography are:
- Secure Communication: Symmetric-key cryptography is used to ensure the confidentiality of communications over the internet, including email, instant messaging, and virtual private networks (VPNs). It is also used to secure voice-over-IP (VoIP) communications and to protect data transmitted between servers and clients.
- File and Data Encryption: Symmetric-key cryptography is used to encrypt files and data stored on computers, mobile devices, and other storage devices. This is particularly important for sensitive data such as financial information, personal information, and medical records.
- Disk Encryption: Symmetric-key cryptography is used to encrypt the entire disk or partition of a computer, which protects data in the event of theft or loss of the computer. This is often used by companies and organizations to protect sensitive information on employee laptops and mobile devices.
- Digital Rights Management (DRM): Symmetric-key cryptography is used in digital rights management to protect copyrighted content, such as music and videos, from unauthorized copying and distribution. This is done by encrypting the content and providing the decryption key only to authorized users.
- Password Protection: Symmetric-key cryptography is used to protect passwords stored in databases and other systems. This is done by encrypting the password and comparing it to the encrypted value when a user logs in.
- Authentication and Authorization: Symmetric-key cryptography is used in authentication and authorization systems, such as smart cards and biometric systems, to ensure that only authorized users can access sensitive information or perform certain actions.
- Secure Sockets Layer (SSL) and Transport Layer Security (TLS): Symmetric-key cryptography is used in SSL and TLS protocols to secure communication between web servers and clients. This is particularly important for e-commerce websites, online banking, and other applications where sensitive information is transmitted over the internet.
Overall, symmetric-key cryptography is essential for ensuring the confidentiality, integrity, and availability of information in various applications.
Limitations of Symmetric-key Cryptography
While symmetric-key cryptography has many advantages, it also has several limitations. Here are some of the main limitations:
- Key Management: In symmetric-key cryptography, the same key is used for both encryption and decryption. Therefore, the key must be kept secret and protected from unauthorized access. Key management becomes more challenging as the number of users and devices increases. It can be difficult to securely distribute keys to all users, and if a key is compromised, all data encrypted with that key becomes vulnerable.
- Limited scalability: Symmetric-key cryptography is not well suited for large-scale deployments. As the number of users and devices increases, the number of keys required to maintain secure communication between them also increases. This can become a logistical and computational challenge.
- Lack of authentication: Symmetric-key cryptography does not provide authentication. This means that the recipient of an encrypted message cannot be sure that the message came from the sender, and not from an imposter who has intercepted the message and decrypted it using the same key.
- Vulnerability to brute force attacks: Symmetric-key cryptography can be vulnerable to brute force attacks, where an attacker tries all possible keys until the correct key is found. The strength of the encryption depends on the key length and the complexity of the encryption algorithm. However, with the increase in computing power, the time required to break the encryption is decreasing.
- Limited functionality: Symmetric-key cryptography is limited in its functionality compared to public-key cryptography. It cannot be used for key exchange, digital signatures, or other advanced cryptographic techniques.
- Lack of forward secrecy: Symmetric-key cryptography does not provide forward secrecy. This means that if a key is compromised, all past and future communications encrypted with that key are also compromised.
Symmetric-key cryptography is a useful tool for securing communication and data, but it has limitations that should be considered when choosing a cryptographic solution. In some cases, a hybrid approach that combines symmetric-key cryptography with public-key cryptography may be more suitable.
Symmetric-key Encryption Algorithms
Symmetric-key encryption algorithms are a class of cryptographic algorithms that use the same secret key for both encryption and decryption of data. Here are some of the most commonly used symmetric-key encryption algorithms:
- Advanced Encryption Standard (AES): AES is a widely used symmetric-key encryption algorithm that is considered to be very secure. It is used in many applications, including secure communications, file and disk encryption, and digital rights management.
- Triple DES (3DES): 3DES is a symmetric-key encryption algorithm that uses three keys and is based on the Data Encryption Standard (DES) algorithm. It is used in many applications, including financial transactions and electronic voting.
- Blowfish: Blowfish is a symmetric-key encryption algorithm that uses variable-length keys and is designed to be very fast. It is used in many applications, including secure communications, file and disk encryption, and password storage.
- Twofish: Twofish is a symmetric-key encryption algorithm that is a successor to Blowfish. It uses 128-bit or 256-bit keys and is designed to be very secure.
- RC4: RC4 is a symmetric-key encryption algorithm that is widely used in secure communications and wireless networks. It is a stream cipher that generates a keystream that is combined with the plaintext to produce ciphertext.
- ChaCha20: ChaCha20 is a symmetric-key encryption algorithm that is designed to be very fast and secure. It is used in many applications, including secure communications and file encryption.
- Salsa20: Salsa20 is a symmetric-key encryption algorithm that is similar to ChaCha20. It is designed to be very fast and secure, and is used in many applications, including secure communications and file encryption.
The choice of symmetric-key encryption algorithm depends on the specific application and the level of security required. AES is currently the most widely used symmetric-key encryption algorithm and is recommended for most applications.
We can categories these type of algorithm as followings:
- Block Ciphers (e.g. AES, DES)
- Stream Ciphers (e.g. RC4)
- Feistel Cipher Structure
- Modes of Operation (e.g. ECB, CBC)
Block Ciphers (e.g. AES, DES)
Block ciphers are a type of symmetric-key encryption algorithm that operates on fixed-length blocks of data. The most widely used block ciphers are AES (Advanced Encryption Standard) and DES (Data Encryption Standard).
AES is a block cipher that uses fixed-length 128-bit blocks of data and supports key lengths of 128, 192, or 256 bits. It is a substitution-permutation network that performs a series of mathematical operations, including substitution, permutation, and mixing, to encrypt data.
DES is an older block cipher that uses fixed-length 64-bit blocks of data and a 56-bit key. It uses a Feistel network structure and performs a series of substitution and permutation operations on the data.
While both AES and DES are block ciphers, AES is considered to be more secure due to its larger block size and longer key lengths. In fact, DES is now considered to be insecure due to advances in cryptanalysis, and AES has largely replaced it as the standard block cipher in use today.
Block ciphers like AES and DES are widely used in applications such as secure communications, file and disk encryption, and digital rights management. However, they do have some limitations, including the need for a secure key exchange mechanism and the vulnerability to certain attacks such as brute-force attacks.
Stream Ciphers (e.g. RC4)
Stream ciphers are a type of symmetric-key encryption algorithm that encrypts data on a bit-by-bit basis, rather than using fixed-length blocks of data. One of the most widely used stream ciphers is RC4.
RC4 is a symmetric-key encryption algorithm that is used in many applications, including secure communications and wireless networks. It generates a keystream that is combined with the plaintext to produce ciphertext. The keystream is generated using a pseudorandom number generator that is seeded with a secret key. The keystream is then combined with the plaintext using bitwise XOR operation to produce the ciphertext.
One of the advantages of stream ciphers like RC4 is that they can be faster and more efficient than block ciphers in some applications, particularly for streaming data such as video and audio. However, stream ciphers can be vulnerable to certain attacks, such as the known plaintext attack, in which an attacker can discover the keystream by observing the ciphertext.
Overall, the choice of stream cipher depends on the specific application and the level of security required. RC4 was widely used in the past but has been found to have certain vulnerabilities, and is no longer recommended for use. More modern stream ciphers, such as ChaCha20 and Salsa20, are now considered to be more secure and are used in many applications today.
Feistel Cipher Structure
The Feistel cipher structure is a widely used design pattern for symmetric-key encryption algorithms, including block ciphers such as DES and Blowfish. It was invented by Horst Feistel in the 1970s and is named after him.
The Feistel cipher structure is based on a series of rounds, each of which consists of two main operations: a substitution (or confusion) operation and a permutation (or diffusion) operation. These operations are performed on a block of plaintext to produce a block of ciphertext.
In the substitution operation, a portion of the plaintext is transformed using a substitution function (also called a substitution box or S-box). The S-box is typically a lookup table that replaces each input value with a corresponding output value. The goal of this operation is to introduce confusion into the plaintext, making it more difficult to recover the original message from the ciphertext.
In the permutation operation, the bits of the partially substituted plaintext are rearranged using a permutation function (also called a permutation box or P-box). The P-box shuffles the bits around, distributing the effect of each bit over multiple bits of the output. The goal of this operation is to introduce diffusion into the plaintext, spreading out the effects of any individual bit change over the entire ciphertext.
The Feistel cipher structure repeats these two operations for a fixed number of rounds, with the output of one round serving as the input for the next. The final output is the ciphertext. To decrypt the ciphertext, the same operations are applied in reverse order.
The Feistel cipher structure has several advantages, including simplicity, parallelizability, and resistance to certain types of attacks, such as differential cryptanalysis. However, it does have some limitations, including the need for a secure key exchange mechanism and the vulnerability to other types of attacks, such as brute-force attacks.
Modes of Operation (e.g. ECB, CBC)
Modes of operation are a way to use block ciphers, such as AES or DES, to encrypt messages of arbitrary length. There are several modes of operation, each with different security properties and performance characteristics. Some commonly used modes of operation are:
- Electronic Codebook (ECB) mode: This mode encrypts each block of data separately and independently of other blocks. The same key is used to encrypt each block. ECB mode is simple and easy to implement, but it is vulnerable to certain attacks, such as pattern recognition, due to its lack of diffusion.
- Cipher Block Chaining (CBC) mode: This mode encrypts each block of data by XORing it with the previous ciphertext block before applying the block cipher. The first block is XORed with an initialization vector (IV) instead of a previous ciphertext block. CBC mode provides diffusion and is resistant to some attacks, such as pattern recognition, but it is vulnerable to certain attacks, such as the padding oracle attack.
- Counter (CTR) mode: This mode turns the block cipher into a stream cipher by generating a keystream using a counter and a secret key. The keystream is XORed with the plaintext to produce the ciphertext. CTR mode provides good performance and parallelizability, but it requires a unique nonce (number used once) for each message and is vulnerable to certain attacks, such as the two-time pad attack.
- Galois/Counter Mode (GCM): This mode is similar to CTR mode but also provides message authentication using a universal hash function. GCM mode is commonly used for authenticated encryption in network protocols, such as TLS.
- Output Feedback (OFB) mode: This mode turns the block cipher into a stream cipher by generating a keystream using the block cipher and an initialization vector (IV). The keystream is XORed with the plaintext to produce the ciphertext. OFB mode provides good diffusion and is resistant to certain attacks, such as the padding oracle attack, but it requires unique IVs for each message and is vulnerable to other attacks, such as the two-time pad attack.
These are just a few examples of modes of operation, and there are many other modes that provide different security properties and performance characteristics. The choice of mode depends on the specific application and the level of security required.
Key Management in Symmetric-key Cryptography
Key management is an essential aspect of symmetric-key cryptography, as the security of the system depends on the confidentiality and integrity of the secret key used for encryption and decryption. Key management involves the following tasks:
- Key generation: Symmetric-key algorithms require a secret key to encrypt and decrypt data. Keys are typically generated using a random number generator or a key derivation function from a secret master key.
- Key distribution: Once the secret key is generated, it needs to be securely distributed to the intended recipients. This can be done using a secure key exchange protocol, such as the Diffie-Hellman key exchange, or by physically delivering the key through a trusted channel.
- Key storage: Secret keys need to be securely stored to prevent unauthorized access. Keys can be stored on secure hardware, such as smart cards or hardware security modules (HSMs), or in software-based key stores protected by access control mechanisms.
- Key usage: Secret keys should be used only for their intended purpose and not shared with unauthorized parties. Applications should use the key only for the required period and destroy it after use.
- Key update and revocation: Secret keys should be updated regularly to maintain security, and compromised keys should be revoked to prevent unauthorized access. Key revocation is particularly important in scenarios where keys are lost, stolen, or compromised.
Effective key management requires a well-designed key management infrastructure and policies that take into account the risks and requirements of the specific application. In addition, key management practices should be regularly audited and tested to ensure their effectiveness and compliance with security standards and regulations.
Key Generation Techniques
Key generation is the process of creating a secret key for use in symmetric-key cryptography. The security of the system depends on the randomness and secrecy of the key. There are various techniques used for key generation, including:
- Random number generation: Random numbers can be generated using hardware or software-based random number generators. These generators use physical processes or algorithms to produce unpredictable and uniformly distributed random numbers.
- Key derivation functions: Key derivation functions (KDFs) can be used to derive a secret key from a master key or a password. KDFs typically use a one-way hash function, such as SHA-256 or HMAC, to transform the input into a random-looking key.
- Pseudorandom number generators: Pseudorandom number generators (PRNGs) can be used to generate a sequence of numbers that appear random but are actually generated using a deterministic algorithm. PRNGs require a seed value that is used as input to the algorithm to generate the random sequence.
- Cryptographic hash functions: Cryptographic hash functions, such as SHA-256 or SHA-3, can be used to generate a fixed-length output that is indistinguishable from random data. The hash function can be applied to a seed value or input data to generate a secret key.
- Physical randomness sources: Physical sources of randomness, such as atmospheric noise or radioactive decay, can be used to generate random data for use as a secret key. These sources are typically used in hardware-based random number generators or true random number generators (TRNGs).
The choice of key generation technique depends on the specific application requirements and the level of security required. A combination of techniques may also be used to ensure the randomness and secrecy of the key. In addition, key generation should be performed in a secure environment to prevent unauthorized access to the key during the generation process.
Key Distribution Techniques
Key distribution is the process of securely transmitting a secret key from the sender to the receiver in symmetric-key cryptography. The security of the system depends on the confidentiality and integrity of the key during transmission. There are several key distribution techniques used in symmetric-key cryptography, including:
- Manual key distribution: Manual key distribution involves physically delivering the key to the intended recipient. This technique is often used in small-scale environments where the number of recipients is limited and the security requirements are not very high.
- Key exchange protocols: Key exchange protocols, such as the Diffie-Hellman key exchange, enable two parties to securely exchange a secret key over an insecure channel. These protocols use mathematical operations to derive a shared secret key that can be used for encryption and decryption.
- Key distribution centers: Key distribution centers (KDCs) are trusted entities that securely distribute secret keys to authorized users. The KDC authenticates the user and provides a secret key that can be used for communication.
- Public key cryptography: Public key cryptography, such as RSA or Elliptic Curve Cryptography, can be used to securely distribute a secret key. This technique involves encrypting the secret key with the receiver’s public key and transmitting the encrypted key to the receiver. The receiver can decrypt the key using their private key and use it for encryption and decryption.
- Hybrid key distribution: Hybrid key distribution combines multiple key distribution techniques to improve security. For example, a key exchange protocol can be used to exchange a temporary session key, which is then encrypted using the receiver’s public key and transmitted to the receiver.
The choice of key distribution technique depends on the specific application requirements and the level of security required. In addition, key distribution should be performed in a secure environment to prevent unauthorized access to the key during transmission. The use of digital signatures, message authentication codes, and secure communication channels can help ensure the confidentiality and integrity of the key during transmission.
Key Storage and Protection Techniques
In symmetric-key cryptography, the security of the system depends on the confidentiality and integrity of the secret key. Key storage and protection techniques are used to safeguard the key from unauthorized access, modification, or destruction. Some common key storage and protection techniques include:
- Key encryption: Key encryption involves encrypting the secret key with a passphrase or another secret key. This technique ensures that the key is not accessible without the passphrase or the secret key used for encryption.
- Hardware security modules: Hardware security modules (HSMs) are dedicated cryptographic devices that provide secure storage and processing of secret keys. HSMs are tamper-resistant and designed to protect against physical and logical attacks.
- Key derivation functions: Key derivation functions (KDFs) can be used to derive a secret key from a master key or a password. The KDFs can be used to generate a key that is specific to the user or the application, and can be used to enhance the security of the key storage.
- Secure storage media: Secret keys can be stored in secure storage media, such as smart cards, USB tokens, or encrypted hard drives. These devices provide secure storage and access control mechanisms to protect the keys from unauthorized access.
- Access control policies: Access control policies can be used to restrict access to the secret key based on the user’s identity, role, or privileges. This can help prevent unauthorized access to the key and ensure that only authorized users can use the key.
- Secure backup and recovery: Secure backup and recovery techniques can be used to ensure that the key is not lost in case of a disaster or hardware failure. Backup copies of the key can be securely stored in a different location, and recovery procedures can be put in place to ensure that the key can be restored in case of a failure.
The choice of key storage and protection techniques depends on the specific application requirements and the level of security required. A combination of techniques may also be used to provide enhanced security for the secret key. In addition, key storage and protection should be regularly audited and tested to ensure that the key remains secure and confidential.
Key Revocation and Replacement Techniques
In symmetric-key cryptography, key revocation and replacement techniques are used to revoke a compromised key and replace it with a new one. This is important to maintain the security and confidentiality of the system in case the key is lost or compromised. Some common key revocation and replacement techniques include:
- Key expiration: Key expiration involves setting a fixed time limit on the usage of the key. After the expiration date, the key is no longer valid and cannot be used for encryption or decryption.
- Key revocation lists: Key revocation lists (KRLs) are lists of revoked keys that are distributed to authorized users. The users can use the KRLs to check if a key has been revoked before using it.
- Key rollover: Key rollover involves replacing a key with a new one before the old key expires. This technique ensures that there is always a valid key available for encryption and decryption.
- Key compromise procedures: Key compromise procedures outline the steps to be taken in case a key is compromised. This may involve revoking the key, generating a new key, and distributing the new key to authorized users.
- Key escrow: Key escrow involves storing a copy of the key in a secure location, such as with a trusted third party. The key can be retrieved in case the original key is lost or compromised.
The choice of key revocation and replacement technique depends on the specific application requirements and the level of security required. In addition, key revocation and replacement should be regularly audited and tested to ensure that the process is reliable and secure. The use of digital signatures, message authentication codes, and secure communication channels can help ensure the integrity and confidentiality of the key revocation and replacement process.
Attacks on Symmetric-key Cryptography
Symmetric-key cryptography is vulnerable to a variety of attacks that can compromise the security of the system. Some common attacks on symmetric-key cryptography include:
- Brute force attacks: Brute force attacks involve trying all possible key combinations until the correct key is found. This attack is effective against weak keys and short key lengths.
- Dictionary attacks: Dictionary attacks involve using a list of common words or phrases to try to guess the key. This attack is effective against weak passwords and passphrases used for key generation.
- Known plaintext attacks: Known plaintext attacks involve using known plaintext and ciphertext pairs to derive the key. This attack is effective when the attacker has access to the plaintext and ciphertext.
- Chosen plaintext attacks: Chosen plaintext attacks involve selecting plaintext and obtaining the corresponding ciphertext to derive the key. This attack is effective when the attacker can choose the plaintext and obtain the corresponding ciphertext.
- Man-in-the-middle attacks: Man-in-the-middle attacks involve intercepting and modifying the communication between the sender and the receiver to obtain the key. This attack is effective when the communication is not encrypted or the encryption is weak.
- Side-channel attacks: Side-channel attacks involve exploiting weaknesses in the physical implementation of the encryption algorithm to obtain the key. This attack is effective against hardware implementations of the algorithm.
To mitigate these attacks, various countermeasures can be employed, such as:
- Using strong keys: Using strong keys with long key lengths and complex key generation techniques can make brute force and dictionary attacks less effective.
- Using secure key distribution techniques: Using secure key distribution techniques, such as public key cryptography, can prevent man-in-the-middle attacks.
- Using strong encryption algorithms: Using strong encryption algorithms with proven security properties can make known plaintext and chosen plaintext attacks less effective.
- Using secure implementation techniques: Using secure implementation techniques, such as hardware security modules, can make side-channel attacks less effective.
- Regularly auditing and testing the system: Regularly auditing and testing the system can identify and fix vulnerabilities before they can be exploited.
By implementing these countermeasures, the security of symmetric-key cryptography can be improved, making it more difficult for attackers to compromise the system.
Strengths and Weaknesses of Symmetric-key Cryptography
Symmetric-key cryptography, like any other cryptographic system, has its strengths and weaknesses. Here are some of the key strengths and weaknesses of symmetric-key cryptography:
Strengths:
- Efficiency: Symmetric-key cryptography is fast and efficient because the same key is used for encryption and decryption. This makes it well-suited for applications that require fast processing of large amounts of data.
- Simplicity: Symmetric-key cryptography is relatively easy to understand and implement, making it accessible to a wide range of users.
- Security: When used correctly, symmetric-key cryptography can provide a high level of security, protecting data from unauthorized access and interception.
- Flexibility: Symmetric-key cryptography can be used in a wide range of applications, from securing communication over networks to encrypting data stored on disk.
Weaknesses:
- Key management: The security of symmetric-key cryptography depends on the security of the key used for encryption and decryption. Managing and distributing keys securely can be challenging, especially in large-scale systems.
- Key exchange: Symmetric-key cryptography requires that the sender and receiver share the same key. Securely exchanging the key can be difficult, especially when the communication channels are not secure.
- Vulnerability to brute-force attacks: Symmetric-key cryptography is vulnerable to brute-force attacks, where an attacker tries all possible key combinations until the correct key is found. This vulnerability can be mitigated by using long keys and strong key generation techniques.
- Lack of non-repudiation: Symmetric-key cryptography does not provide non-repudiation, which means that it cannot prevent the sender from denying that they sent a message.
- Lack of scalability: Symmetric-key cryptography is not well-suited for large-scale systems because the number of keys required increases exponentially with the number of users.
Overall, symmetric-key cryptography is a powerful and widely used cryptographic system. While it has its limitations, many of these can be mitigated by using best practices for key management, key exchange, and key generation. By understanding the strengths and weaknesses of symmetric-key cryptography, users can make informed decisions about when and how to use this technology to secure their data.
Real-world Applications of Symmetric-key Cryptography
Symmetric-key cryptography is widely used in many real-world applications where confidentiality and integrity of data are critical. Here are some examples:
- Secure communication over networks: Symmetric-key cryptography is used to encrypt data transmitted over the internet, including email, instant messaging, and web browsing. Examples of protocols that use symmetric-key cryptography for encryption include SSL/TLS, IPSec, and SSH.
- Data storage: Symmetric-key cryptography is used to encrypt data stored on disk, including databases and individual files. This provides an extra layer of security in case the physical storage media are stolen or compromised.
- Payment processing: Symmetric-key cryptography is used to secure payment transactions over the internet. Examples of payment protocols that use symmetric-key cryptography for encryption include SET (Secure Electronic Transaction) and SSL/TLS.
- Smart cards: Symmetric-key cryptography is used in smart card systems, such as credit cards and ID cards, to secure the information stored on the card and prevent unauthorized access.
- Digital rights management: Symmetric-key cryptography is used to protect digital content, such as movies, music, and e-books, from unauthorized copying and distribution.
- Military and government applications: Symmetric-key cryptography is used extensively by military and government organizations to secure confidential data, including communications, intelligence, and surveillance.
Overall, symmetric-key cryptography plays a critical role in securing many real-world applications where confidentiality and integrity of data are essential. Its efficiency, simplicity, and security make it a popular choice for many organizations and users.
Summary
Symmetric-key cryptography is a cryptographic system that uses the same key for both encryption and decryption of data. It is widely used in many real-world applications where confidentiality and integrity of data are critical, such as secure communication over networks, data storage, payment processing, smart cards, digital rights management, and military and government applications.
Symmetric-key cryptography has several strengths, including efficiency, simplicity, security, and flexibility. However, it also has limitations, such as key management, key exchange, vulnerability to brute-force attacks, lack of non-repudiation, and lack of scalability.
Overall, understanding the strengths and weaknesses of symmetric-key cryptography is crucial for making informed decisions about when and how to use this technology to secure data. By using best practices for key management, key exchange, and key generation, users can mitigate many of the limitations and ensure the confidentiality and integrity of their data.
FAQ with Q&A
Some frequently asked questions and their answers related to symmetric-key cryptography.
Q: What is symmetric-key cryptography?
A: Symmetric-key cryptography is a cryptographic system that uses the same key for both encryption and decryption of data.
Q: How does symmetric-key cryptography work?
A: In symmetric-key cryptography, the sender and receiver use the same key to encrypt and decrypt the data. The key is kept secret and known only to the sender and receiver.
Q: What are some examples of symmetric-key encryption algorithms?
A: Some examples of symmetric-key encryption algorithms include AES (Advanced Encryption Standard), DES (Data Encryption Standard), and Blowfish.
Q: What are the limitations of symmetric-key cryptography?
A: Some limitations of symmetric-key cryptography include key management, key exchange, vulnerability to brute-force attacks, lack of non-repudiation, and lack of scalability.
Q: What are the strengths of symmetric-key cryptography? A: Some strengths of symmetric-key cryptography include efficiency, simplicity, security, and flexibility.
Q: What are some real-world applications of symmetric-key cryptography?
A: Some real-world applications of symmetric-key cryptography include secure communication over networks, data storage, payment processing, smart cards, digital rights management, and military and government applications.
Q: How can users ensure the security of symmetric-key cryptography?
A: Users can ensure the security of symmetric-key cryptography by using best practices for key management, key exchange, and key generation.
Q: What is the difference between symmetric-key cryptography and asymmetric-key cryptography?
A: In symmetric-key cryptography, the same key is used for both encryption and decryption, while in asymmetric-key cryptography, different keys are used for encryption and decryption. Asymmetric-key cryptography provides additional security features, such as digital signatures and key exchange, but is less efficient than symmetric-key cryptography.
Valuable information. Lucky me I found your website by accident, and I’m shocked why this accident did not happened earlier! I bookmarked it.
My spouse and I stumbled over here different web page and thought I might check things out. I like what I see so i am just following you. Look forward to finding out about your web page for a second time.
I am now not positive the place you’re getting your information, but good topic. I needs to spend some time studying much more or figuring out more. Thank you for magnificent information I used to be looking for this info for my mission.
Wow, fantastic blog layout! How long have you been blogging for? you made blogging look easy. The overall look of your site is excellent, as well as the content!
Thank you for your articles. I find them very helpful. Could you help me with something?
I’m so in love with this. You did a great job!!
It抯 actually a cool and useful piece of information. I抦 glad that you shared this helpful information with us. Please keep us informed like this. Thanks for sharing.
Thanks for your tips. One thing I have noticed is that banks in addition to financial institutions have in mind the spending behaviors of consumers plus understand that many people max outside their cards around the vacations. They correctly take advantage of this specific fact and begin flooding your current inbox and also snail-mail box along with hundreds of Zero APR card offers just after the holiday season comes to an end. Knowing that for anyone who is like 98 of all American general public, you’ll jump at the possible opportunity to consolidate credit card debt and switch balances to 0 APR credit cards.
Good day! I know this is kinda off topic however , I’d figured I’d ask. Would you be interested in trading links or maybe guest writing a blog article or vice-versa? My blog discusses a lot of the same subjects as yours and I believe we could greatly benefit from each other. If you’re interested feel free to shoot me an email. I look forward to hearing from you! Superb blog by the way!
Awsome info and right to the point. I am not sure if this is in fact the best place to ask but do you folks have any ideea where to hire some professional writers? Thanks in advance 🙂
Good blog post. A few things i would like to contribute is that laptop memory needs to be purchased in case your computer can no longer cope with what you do along with it. One can put in two RAM boards having 1GB each, as an illustration, but not certainly one of 1GB and one with 2GB. One should look for the car maker’s documentation for the PC to make sure what type of memory is essential.
mail me to the hemantkavi@gmail.com or admin@myonlinevidhya.com
hello there and thank you for your info ?I have certainly picked up something new from right here. I did however expertise several technical points using this website, since I experienced to reload the site lots of times previous to I could get it to load properly. I had been wondering if your hosting is OK? Not that I’m complaining, but slow loading instances times will sometimes affect your placement in google and could damage your high-quality score if advertising and marketing with Adwords. Anyway I am adding this RSS to my email and could look out for much more of your respective exciting content. Ensure that you update this again very soon..
Valuable information. Lucky me I found your website by accident, and I am shocked why this accident didn’t happened earlier! I bookmarked it.
I used to be recommended this website via my cousin. I am not positive whether or not this publish is written by means of him as nobody else recognize such designated about my trouble. You’re amazing! Thanks!
Your articles are extremely helpful to me. May I ask for more information?
Your articles are extremely helpful to me. Please provide more information!
Thank you for your articles. I find them very helpful. Could you help me with something?
I want to thank you for your assistance and this post. It’s been great.
Thank you for your post. I really enjoyed reading it, especially because it addressed my issue. It helped me a lot and I hope it will also help others.
Can you write more about it? Your articles are always helpful to me. Thank you!
Your articles are extremely helpful to me. Please provide more information!
I do not know if it’s just me or if everybody else encountering problems
with your site. It appears as though some
of the written text on your posts are running off the screen. Can someone else please comment and
let me know if this is happening to them too? This may
be a problem with my browser because I’ve had this happen previously.
Thanks
[…] Symmetric Key […]
Thank you for providing me with these article examples. May I ask you a question?
Yes
[…] Symmetric-key cryptography […]